Introduction
We have posed three questions in our series on information security so far:
- What is your most valuable and sensitive information?
- Where is this information?
- Where should this information be?
At this point, you should be able to identify your most-important information, locate it, and reduce its footprint to the minimum necessary to realise its value. The next step is to consider:
- What information security goal do you seek to achieve?
Goals
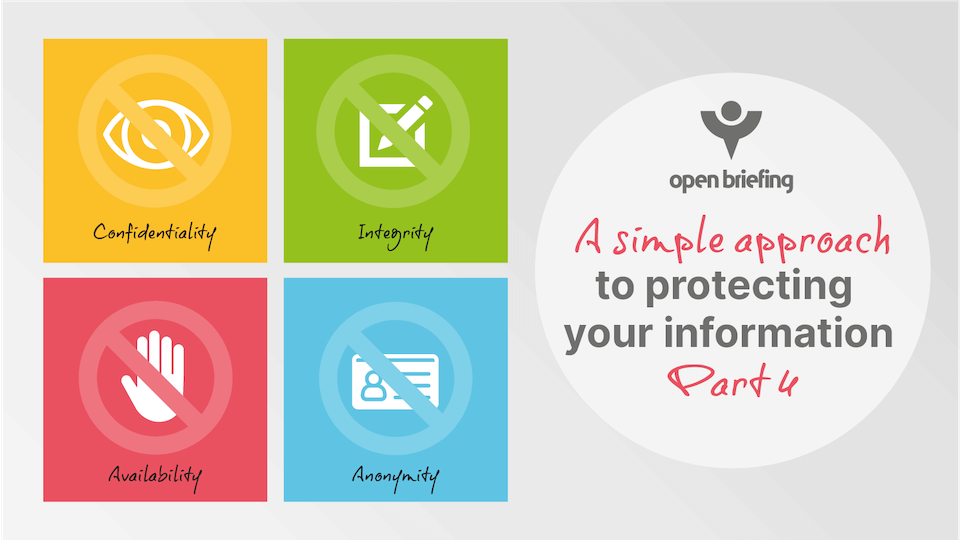
 It is important to determine the primary goal of your information security measures before deciding which ones to implement. Traditionally, this would be one of three goals, known as the CIA triad:
It is important to determine the primary goal of your information security measures before deciding which ones to implement. Traditionally, this would be one of three goals, known as the CIA triad:
- Confidentiality. Protecting information from unauthorised access or disclosure.
- Integrity. Protecting information from unauthorised modification or alteration.
- Availability. Ensuring authorised activities with the information can take place and are not denied.
For activists and nonprofits working in closed civic spaces or on rights and justice issues, it is often necessary to consider an additional goal:
- Anonymity. Protecting the identity of parties or the links between them.
Determining the Goal
You should decide on a primary goal for each of your most valuable and sensitive information assets. You can then implement security measures to achieve this goal and ensure that other security measures do not conflict with this goal, or at least, if they do, that the risk is acceptable.
Over a long enough timeframe, all information will either be made public or be destroyed. If the information is public, then adversaries can definitely access it and the identified harm may be virtually certain to occur. If it is destroyed, then you definitely cannot use it to achieve the positive change in the world that your adversaries want to avoid. When deciding on the goals of your security measures, you may wish to determine which of these two outcomes would be best (or the least worst). There are many ways to fail, so fail well!
If it would be better for information to become public than destroyed, then availability and integrity are likely to be important; however, if it would be better for information to be destroyed than made public, then confidentiality and anonymity are likely to be important.
Anonymity is typically the hardest goal to achieve. Many technologies must use unique identifiers to ensure messages are routed to the correct person or device. These identifiers potentially reveal the person using a device, the device itself, and the parties interacting. Given the difficulty of ensuring anonymity, you should check if there are already other means to identify parties or the links between them, such as tax returns or international bank transfers. If so, then anonymity may have already been compromised.
Once you have identified your security goal, it might be necessary to revisit the question posed previously in this series: where should the information be? For example, it may now be necessary to implement secure backups, and so the number of locations where your information should be will increase.
Conflicting Goals
It may be tempting to try and achieve most – or even all – of these goals each time, but this is rarely possible. The measures used to achieve one goal will generally make no improvement for the other goals – in fact, they will likely undermine them.
Consider a scenario where the security goal is the confidentiality of an information asset (i.e. you want to protect it from unauthorised access). This is typically the first (and only) aspect of information security that people think of. In general, encryption is an excellent security measure to achieve this goal. But suppose that only one copy of the information exists and it is encrypted – what happens if you forget the password? That information asset is not accessible any more, so availability is negatively impacted (i.e. authorised activities with the information cannot take place).
Conversely, if availability is the security goal, you might distribute multiple copies of the information in many locations in order to achieve it. But then the likelihood of a breach increases dramatically, and so confidentiality is negatively impacted. (Note, availability can, of course, be undermined without confidentiality being breached, for example in the case of a Distributed Denial of Service attack.)
In these scenarios, achieving both confidentiality and availability with confidence is challenging.
A note on collaboration
As covered previously, information can be in a variety of states and locations. Some of these will be under your control, some you will have limited control over, and others you will have no control over. To realise the value of your information, you may need to share it with another organisation. Unfortunately, you cannot ensure that they have the same information security goal as you and are implementing equivalent security measures. If that information is sensitive, you will need to consider whether to share it with them in the first place.
Remember, your adversaries will not limit their attention to you or your organisation, but will instead look at the bigger picture – because they may be able to achieve their goals without involving you at all.
Conclusion
You must assume that adversaries are rational and will seek to find vulnerabilities that breach the confidentiality, integrity, availability, and anonymity of your valuable and sensitive information. They may not be the one to cause the breach, and publication of your information in an untargeted data dump (or even unintentionally by you) may be just as harmful. Equally, the breach may come from a partner organisation and not be under your control.
Whether targeted or untargeted, an attack will focus where your information security is weak not where it is strong. Your approach must match this rationality. It starts with identifying the goal of your security measures. When you know what security measures should achieve, you can make an informed and rational decision on what to implement, and also accept the inevitable negatives that come with those measures.
In the next article, we will look at the types of security measures you might consider.
